A Hack-for-Hire Group is Specializing in Targeting Canada
Sophos research shows that a ransomware group is targeting Canada 80% of the time
Canadian Cyber in Context is sponsored by
All views expressed belong to Canadian Cyber in Context and do not reflect the position of any sponsor.
Have your business featured in Canadian Cyber in Context with a sponsorship.
In early 2025, a new, distinct ransomware known as QWCrypt began to be identified by cyber security researchers. What stood out to researchers was that QWCrypt is deployed by the threat group GOLD BLADE (also known as RedCurl and RedWolf) and is a departure from their previous methods. Since 2018, GOLD BLADE has predominantly focused on espionage and the theft of sensitive data, so the deployment of ransomware marked a significant departure from its usual modus operandi. While some researchers have stated that GOLD BLADE is a Russian-speaking group, Sophos has stated it has not seen sufficient evidence to confirm or deny this.
However, despite the theft of data, there was no previous evidence to indicate that the group’s business model entails. Due to the lack of a data-leak site or other means to sell the stolen data back, both Bitdefender Labs and Sophos have suggested that the GOLD BLADE is a hack-for-hire group, essentially making it a mercenary group. Alternatively, despite the lack of a leak site, in March 2025, Bitdefender Labs hypothesized that GOLD BLADE may be specifically trying to be discreet and avoid public attention to increase the likelihood of payout by allowing the targeted business to keep the incident quiet.
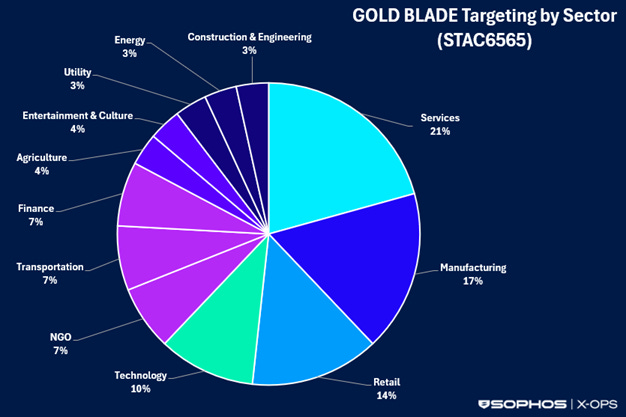
On December 5, cyber security firm Sophos released research that agreed with Bitdefender’s assessment that evidence suggests GOLD BLADE is likely a hack-for-hire group that specializes in discreet operations. More concerning for Canadians, Sophos found that GOLD BLADE targets Canada in approximately 80% of its attacks. However, GOLD BLADE does not deploy ransomware in all of its attacks, but appears to ransomware victims selectively, which Sophos suggests may be GOLD BLADE independently monetizing its intrusions in addition to conducting espionage for its clients.
Of particular concern is the manner in which GOLD BLADE appears to be a skilled professional operation. GOLD BLADE will periodically go “dormant” for a period of months without new attacks or intrusions, but return with new and improved tactics. Since they were first observed in 2018, GOLD BLADE have steadily innovated and improved its tactics and methods. Historically, GOLD BLADE relied on social engineering and spear-phishing to gain initial access to targets using fake CVs and resumes infected with malware, but they have since evolved their tactics to target third-party recruitment platforms like Indeed, JazzHR, or ADP WorkforceNow.
On November 26, Minister of National Defence David McGuinty and Minister of Public Safety Gary Anandasangaree released a joint statement warning about the rise in malicious cyber activity targeting Canadian critical infrastructure. This joint statement wasn’t released just because of GOLD BLADE, but GOLD BLADE is a symptom of a larger problem of growing cyber attacks on Canadians. GOLD BLADE’s targets are not limited to a specific sector but span a wide array of businesses, including some critical infrastructure. The hyper-specific targeting methods of GOLD BLADE suggest these attacks are deliberate rather than opportunistic.
This ultimately begs the question, who is paying a hack-for-hire group to target Canadian organizations 80% of the time? This is where I think the real discussion begins. GOLD BLADE’s methods of lying dormant, only to return with improved, discreet methods, may indicate this is a business or contractor. If GOLD BLADE is indeed a hack-for-hire group, the nearly 80% targeting of Canada may indicate either a limited number of clients or a single client who is specifically hiring them to target Canada. Based on this, and Group-IB’s analysis that GOLD BLADE is a Russian-speaking group, it could mean that GOLD BLADE is a Russian contractor receiving direction from Russian intelligence services. GOLD BLADE’s innovation and growth into ransomware to supplement its activities are in line with many Russian state-sponsored groups, which often receive considerable leeway from the government to conduct ransomware operations against Western countries. This remains merely a hypothesis and speculation at this stage, but it would align with Russia’s increasing investment and use of non-state actors and contractors to conduct cyber operations on behalf of the state.
Take Aways
It is not surprising that specific hack-for-hire groups are beginning to specialize in certain geographic regions or countries. GOLD BLADE has historically targeted predominantly Western countries, including the United States, Australia, and the United Kingdom, with the focus on Canada only being a recent development. As Russia and China continue to make use of contractors and non-state actors to conduct operations against the West, contractors will increasingly specialize in their methods and tools to be able to target specific countries and sectors to be more competitive in markets that are increasingly becoming inundated with non-state actors offering hack-for-hire services for Russia and China.
The delays in getting Bill C-8 and the Critical Cyber Systems Protection Act passed by Parliament seriously limit the federal government’s ability to better address national cyber security. However, with the ongoing civil liberties concerns over the secret, binding cyber security directions that Bill C-8 would allow, it is not a surprise that there has been little movement.
Stay vigilant during December. Cyber threat actors love December and the holidays because IT departments are more likely to be on holiday/vacation, allowing threat actors to operate in networks with more impunity.
The international hack-for-hire scene is still relatively nascent/small, but this might be the first instance of a hack-for-hire group specializing in targeting Canada. It is not unheard of for cyber threat actors to specialize in targeting certain geographic regions or sectors. However, Canada is usually bundled with other English-speaking or Western countries, so it is unusual to see a specific group target Canada in such a manner.
It is not unheard of for Canadians to be convicted of ransomware crimes, but ransomware criminals tend to be more opportunistic than targeted, unlike GOLD BLADE.
If you are a Canadian business, review your cyber security controls, tools, and processes (especially if you use recruitment platforms).
Cyber security is part of doing business, and the cyber threat environment is getting more dangerous; all businesses need to ensure their investment in cyber security is appropriate to the amount that they use cyberspace.
Sophos has three primary recommendations they say are effective against common GOLD BLADE attacks:
Improve recruitment security workflow. Either ensure that all attachments are routed through email or another secure gateway for review/scanning, or require the use of secure document viewers.
Prioritize endpoint coverage and monitoring. Ensure all endpoints are centrally managed, kept up to date, and that comprehensive logs are maintained.
Implement a managed detection and response solution. Detection and blocking are key, but detection must be followed up with active monitoring, investigation, and response.
The Canadian Centre for Cyber Security have provided a backgrounder on the attacks on Canadian critical infrastructure and ways that operators can do to better protect their networks.
Don’t Forget the Survey!
Please spare some time for the Canadian Cyber in Context’s year-end survey to help us better cater our 2026 content for you.
Fill out the survey here