Canadian Cyber News Rewire - 7/02/26
Wiring you into the cyber news relevant to Canada the week ending February 7
The Weekly New Rewire is a survey of cyber or adjacent news stories that I read this week (or recently). Please leave a comment if you think I missed anything.
Editor Notes:
Thank you to those that filled out the Cyber News Rewire survey! Respondents favored releasing the Rewire on Monday, which will be the release day going forward. The survey will remain open and I will share it periodically.
I had my wisdom teeth removed last week, so this Rewire and next might be a little light side as I recover.
Canadian News
Canada Is Building a Surveillance Network in Space
The great Wesley Wark discusses how and why Canada is developing surveillance satellites to reduce dependence on allies and increase Canadian sovereignty and situational awareness. Cyber security for satellites is increasing in importance and remains a major gap area for protections compared to other areas. Over the last few years as attacks have increased, things have improved, but satellites of all types are increasingly becoming a lynchpin for militaries. People are growing aware and things are shifting towards the better, but we’re barely making progress.
WhatsApp releases account feature that looks to combat spyware
WhatsApp is a common vector for attacks, so anything to improve security in encrypted messaging apps is good.
‘Chilling’ hacking network is targeting vulnerable children, charity warns
This is an article focused on the UK, but the group discussed here (The Com) is also targeting Canada and Canadians. One of the worst, most despicable threat actors whose members often targets children for extortion and to show off.
AI and Digital Defence: Canada Among the Global Elite
“A Canadian Army team attended the event and showcased their AI-powered cyber defence system, which earned first prize at the NATO TIDE Hackathon in France earlier this year.”
This is cool stuff, but I believe this is a prototype and not in widespread use yet. There is a mention of CloudTAK, a cloud-based tactical network, which started in a similar small testing and now is in pretty widespread use.
Building with AI is now the “price of admission” for software startups, Inovia report says
AI for the sake of AI is leading to the creation of a bubble. Yes, AI can produce great things with productivity gains. However, this is not a given. Not all AI products are made the same and there is a lot that really sucks. And even amongst the models that do work well, their application are very narrow and there remains a lot unintentional errors in LLM. This will produce more bad than good.
Earth is full of power-hungry data centres. Is shooting them into space the answer?
No. Full stop. This is a hole to waste money and time. Data centres in space would be more expensive and have far less capacity. All you’re doing is creating more congestion in orbit.
Substack data breach exposed users’ emails and phone numbers
Our emails and phone numbers were stolen in a Substack data breach. It sounds like this was data scrapping and login credentials and financial information was not obtained, but the information obtained could still enable criminals to commit fraud.
A major part of Canada’s latest National Cyber Security Strategy was to provide Cyber Attribution Data Centre (CADC) at the Canadian Institute for Cybersecurity (CIC) at the University of New Brunswick. The government is providing $10 million over 5 years to fund this project, which I hope is the start of things as the CADC has potential to do global good. The idea behind the CADC is to collect and analyze data on cyber attacks to improve the attribution and our collective understanding of cyber attacks.
Nearly 1,300 customers affected by Canada Computers data breach, company says
More developments on this story. 1,300 customers affected by card skimming, which feels like a low estimate for a national brand whose website was affected during the holidays.
Y Combinator reverses decision, will invest in Canadian-domiciled startups again
This decision is quite confusing. Y Combinator president claims the move was because all its top-performing Canadian companies reincorporate in the US. Yet, he also claimed that they weren’t saying “not saying Canadians should leave Canada,” just that “Where you are incorporated increases your access to capital. That’s it.” In other words, they got a lot of heat and are backpedaling due to their decision. For people with a lot of access to capital, they seem to lack a spine like most American corporations at the moment.
This should be a wake up call for the Canadian ecosystem to build the means to bring capital to Canada, not to authoritarian states.
N.B. government will no longer use X after child and youth advocate raises concerns
New Brunswick shows that it cares more about stopping deep fake child sexual pornography than the federal government as Minister of AI Evan Soloman still proclaims his love for the platform that produced deep fake child pornography for profit.
Insider risk — Security starts with you
DND releases article on insider threat/risks. Cyber threat actors, particularly ransomware, are increasingly looking for insiders to provide them access in exchange for a kickback.
Ransomware Threat Outlook 2025-2027
“We assess that threat actors carrying out ransomware attacks impacting Canadian organizations are almost certainly opportunistic and financially motivated. All Canadian organizations, regardless of size or sector, are at risk of being targeted by ransomware. In addition to impacting the infrastructure, data, supply chain, and operations of organizations, a ransomware attack can also impact Canadians’ livelihoods by disrupting the critical services they depend on.”
Canada continues to be a favorite target for ransomware operators. Like all other threat actors, they’re now using AI tools as well.
The quantum era is coming. Are we ready to secure it?
Quantum technology is advancing quite steadily. We will see the slow integration of quantum sensing and related technology in the next 5 years, which will increasingly risk cyber security long before quantum computers will be worthwhile.
Canada’s digital sovereignty dilemma
Honestly, not a great article (it’s really just the opening for a newsletter), but summarizes a lot of the variables. What is missed from this is how a lot of the standing Canadian policies on digital sovereignty does not even ensure Canadian digital sovereignty in the first place. As long as the software, infrastructure, or anything used is owned by a US corporation, it risks Canadian sovereignty as it forces the corporation to turn any data over to the United States due to a “criminal investigation.” The corporations will claim they it doesn’t “force” them, but it does if they do not decide to fight it in court. It thus means that you have to trust the United States judicial system to treat this accordingly and that the corporation will refuse and fight it. I will then ask you if you trust the current United States justice department and United States-based corporations?
If you do, then I have a million dollar idea to sell you, you mark.
ISED releases Summary of Inputs for Canada’s next AI Strategy
Results aren’t too surprising. Businesses want unfettered investment and growth without a care of how AI impacts anyone but them, whereas public institutions wants a coordinated response that regulates AI to offset the negatives. With Evan Soloman at the helm, we are likely to see things lean towards doing whatever businesses want and ignore the major negative impacts on the rest of society. I’ll be shocked if anything rational and nuanced is done comes out of this government on AI.
A very interesting event coming up. There’s been an explosion of hack-a-thons over the past year, especially focused on defence. This might be the first red team-focused one I have seen, or at least advertised.
Canada Cyber Threat Watch
While not all attacks are reported or receive media attention, any notable or open-source cyber attacks on Canadian organizations and any relevant cyber threat intelligence to Canada will be posted here. I only list the Canadian Centre for Cyber Security’s (CCCS) alerts here, not all advisories; follow the full feed here.
Notepad++ Hijacked by State-Sponsored Hackers
Hosting provider was compromised leading to Notepad++ being attacked. They have since changed hosting providers. Another supply chain attack, which attempted to hijack the update process for older versions of Notepad++. Suggests that it was a Chinese APT, which is not a surprise based on the TTPs.
Russian hackers exploit recently patched Microsoft Office bug in attacks
When we are all dead and gone, the only thing that will remain are Microsoft Office bugs and exploits.
Wave of Citrix NetScaler scans use thousands of residential proxies
Citrix is often targeted by cyber threat actors due to its use by so many businesses. Scanning on this scale means a well resourced threat actor, which GreyNoise is specifically calling this an indication for pre-exploitation.
Lakelands Public Health: Infectious disease data safe from cyberattack, Ontario public health unit says
Qilin Ransomware Strikes Ontario Workers Health & Safety Centre
Canadian Centre for Cyber Security: Security considerations for edge devices
As the United States pulls edge devices, CCCS has released a guidance document with international partners on how to protect edge devices.
Flickr discloses potential data breach exposing users’ names, emails
DND/CAF use Flickr quite a bit, so I hope this is on their radar. Looks like logins are safe, but still a decent amount of details captured that could enable fraud or phishing.
Have your business and logo featured in Canadian Cyber in Context with a sponsorship.
Research and Op-Eds
Max Smeets’ Keynote at Black Hat Europe 2025 (60 minute keynote talk)
Max Smeets is the best political scientist researching cyber conflict today. Anything his name is attached to is worth a read/listen/watch.
China’s Intelligence Community: An Overview
Over the last decade, China has completely reorganized its military and intelligence communities, including how it uses cyber operations. This reorganization, along with major investments into building an offensive security industry, has contributed to China’s massive success with cyber operations in the past 6 years. If you thought China was prolific in industrial espionage in the 90s, that has nothing on what they’re doing today.
How European and allied cybersecurity strategies are shifting from defence to offence
The shift from pure defence to incorporating offensive is because only relying upon defence means you’re allowing threat actors the initiative to constantly attack you without stopping their means to constantly attack you. Western countries are still trying to figure out how to scale their offensive operations because it is difficult skill to master, but also Western countries primarily relegate offensive operations to their signals intelligence organization and military, which is often difficult to recruit individuals for because the private sector pays so much more and the heavy restrictions as a government employee or military member is a hard sell. (I am literally finishing my dissertation on this, so I could talk all day about this.)
United States News
StopICE App blames hack on “a CBP agent here in SoCal.”
StopICE, an app that helps Americans track the location of US ICE raids has had a security breach, which they have blamed on a Customs and Border Protection agent. This is part of a series of attacks by partisan hackers on apps or websites that helps Americans track the activities of ICE.
NSA Releases First in Series of Zero Trust Implementation Guidelines
Something I missed from last month. The NSA is released a series of guides on zero trust architecture, which is essentially becoming the default architecture for all networks.
Exclusive: Pentagon clashes with Anthropic over military AI use, sources say
This is how the United States will continue to have significant control and influence over Canad. By relying upon United States technology and corporations, the United States’ continued descent into authoritarianism risks compromise a lot of information and communications technology. The United States’ support of science denialism and attempt to control what chat bots says will mean that AI LLMs and others which adhere to these principles of denialism and lies cannot be trusted and will ultimately make those who use them dumber.
FCC urges telecoms to boost cybersecurity amid growing ransomware threat
Telecoms in North American, including Canada, are increasingly targeted by cyber threat actors, particularly China’s Volt Typhoon. Despite what Canadian telecoms will lie telling you, they have been victims of these attacks.
FBI Couldn’t Get into WaPo Reporter’s iPhone Because It Had Lockdown Mode Enabled
Lockdown mode was originally developed to prevent remote access spyware, but increasingly is shown to help prevent authoritarian regime thugs from accessing a journalist’s phone they physically have.
Exclusive: US used cyber weapons to disrupt Iranian air defenses during 2025 strikes
The #1 target for cyber operations during a conflict are air defences. This has been happening for over 20 years. The earliest public one we know of is Israel taking down Syrian air defenses when they bombed their nuclear facilities.
Department of Defense Establishes CYBERCOM 2.0 - Revised Cyber Force Generation Model
DOD releases implementation overview for CYBERCOM 2.0 with three pillars: domain mastery; specialization; agility. Some interesting stuff in this plan, but will like save it for a research article to unpack for implications for Canada/CAFCYBERCOM. Won’t affect Canada much, but may influence future CAF cyber force development.
ICE and CBP’s Face-Recognition App Can’t Actually Verify Who People Are
This is the case for a lot of this type technology and cannot be trusted, just like the people using it.
BOD 26-02: Mitigating Risk From End-of-Support Edge Devices
CISA issues binding order for the removal of edge devices that are no longer supported by the developer. Edge devices refers to networking devices on the outer “edge” of your network that
Penn’s October data breach impacted fewer than 10 people, despite hackers’ claims it was 1.2 million
I really like this article because it highlights something that all ransomware groups do: lie. They’re going to lie to you about how bad the attack is, they’re going to lie that there’s nothing you can do, they’re going to lie that they’ll unlock everything if you pay. The criminal will say and do anything to do a payment from you.
If worse case scenario happens and you are hit with ransomware with a criminal that wants to negotiate, listen to WOPR: The only winning move is to not play. (If you don’t understand this reference, I recommend watching the historically important hacking movie of WarGames.)
Homeland Security is trying to force tech companies to hand over data about Trump critics
This is precisely why you cannot trust US-based corporations at the moment when they claim they will not just hand information over to the government. The United States government is already abusing the system to request information on its citizens. They will have even less qualms in demanding non-citizen data if they deem it necessary. There is no “but,” this is a United States administration actively seeking to break or stretch the law in ways it was not intended to intimidate, threaten, and turn the United States into an authoritarian state. This will only get worse.
US military used new ‘non-kinetic’ cell to guide cyber ops during Maduro capture
Similar groups have been used before at lower operational and tactical levels, so it is not surprised there is now one at the Pentagon for strategic and operational oversight of the whole of the forces to help guide. Western militaries overall are moving in this direction, particularly with Cyber Electromagnetic Activities (CEMA) which is the overlapping functions and use of cyber and traditional electronic warfare capabilities. This is a big reason why CAFCYBERCOM has charge of cyber and electro-magnetic capabilities, with eletro-magnetic being a big area for attention to grow right now based on learned experiences from Ukraine.
Payments platform BridgePay confirms ransomware attack behind outage
What would happen if a similar attack targeted Interac in Canada?
European Union & United Kingdom News
Ukraine to share wartime combat data with allies to help train AI
The future of warfare is in big data analytics and AI/ML. Not surprising Ukraine is attempting to leverage this. I am more surprised it took them this long and I hope they receive a lot of money for this data.
Fancy Bear Exploits Microsoft Office Flaw in Ukraine, EU Cyber-Attacks
Fancy Bear is a Russian military cyber unit. Good to keep in mind that Russia continues to focus is cyber activities on Ukraine, which faces
Nobel Committee says Peace Prize winner likely revealed early by digital spying
“And while financial bets were placed, it was not known whether the ultimate purpose was to profit from the incident or to inflict damage to the credibility of the prize”
They seem to be suggesting they either think the hack is linked to polymarket betting or a state actor conducting a hack and leak operation. Either is a major possibility. I can definitely see both of them being likely, but the financial aspect seems the most likely.
Police Raid Elon Musk’s X Paris Office in Criminal Probe
French police raid Twitter (X) offices in France as part of investigation into systematic, authorized production and profiting from Child Sexual Abuse Material (CSAM) by Grok and other alleged crimes.
France releases National Cybersecurity Strategy
I am not too familiar with specifics of French policy, but I do like this strategy. However, reading it makes me depressed about just how bad Canada’s most recent National Cyber Security Strategy is and how much we lost out and continue to lose out from the Canadian government treating cyber security as a tertiary issue.
Ukraine hails ‘real results’ after Musk restricts Russian Starlink use
After reports that Russia was using Starlink for drones, an update was pushed to prevent the use of starlink on vehicles moving faster than 75 km/hr.
Danish Defence Intelligence Service open applications for its Hacker Academy
Italy claims cyberattacks ‘of Russian origin’ are pelting Winter Olympics
Olympic Destroyer 2. Russia targeted the Japan Olympics a few years ago as well.
One of Europe’s largest universities knocked offline for days after cyberattack
La Sapienza in Rome hit with ransomware. Everyone is a target, especially public institutions. Invest in cyber security or you’re next.
Rebooting the UK’s Cyber Strategy
A good write up about the UK’s new cyber strategy.
“The paper calls for bold action to address market failures, enhance resilience and ensure the UK is prepared to tackle evolving cyber threats. It provides a roadmap for policymakers to protect critical infrastructure, secure economic growth and safeguard national security in an increasingly uncertain global landscape.”
Commission responds to cyber-attack on its central mobile infrastructure
Other International News
A fascinating read of individuals traveling to Chengdu, China to do site visits to Chinese APTs.
Full write up here:
Cyberattack in Senegal: DGID targeted by Black Shrantac group
Major attack on Senegal’s government
Have your business and logo featured in Canadian Cyber in Context with a sponsorship.
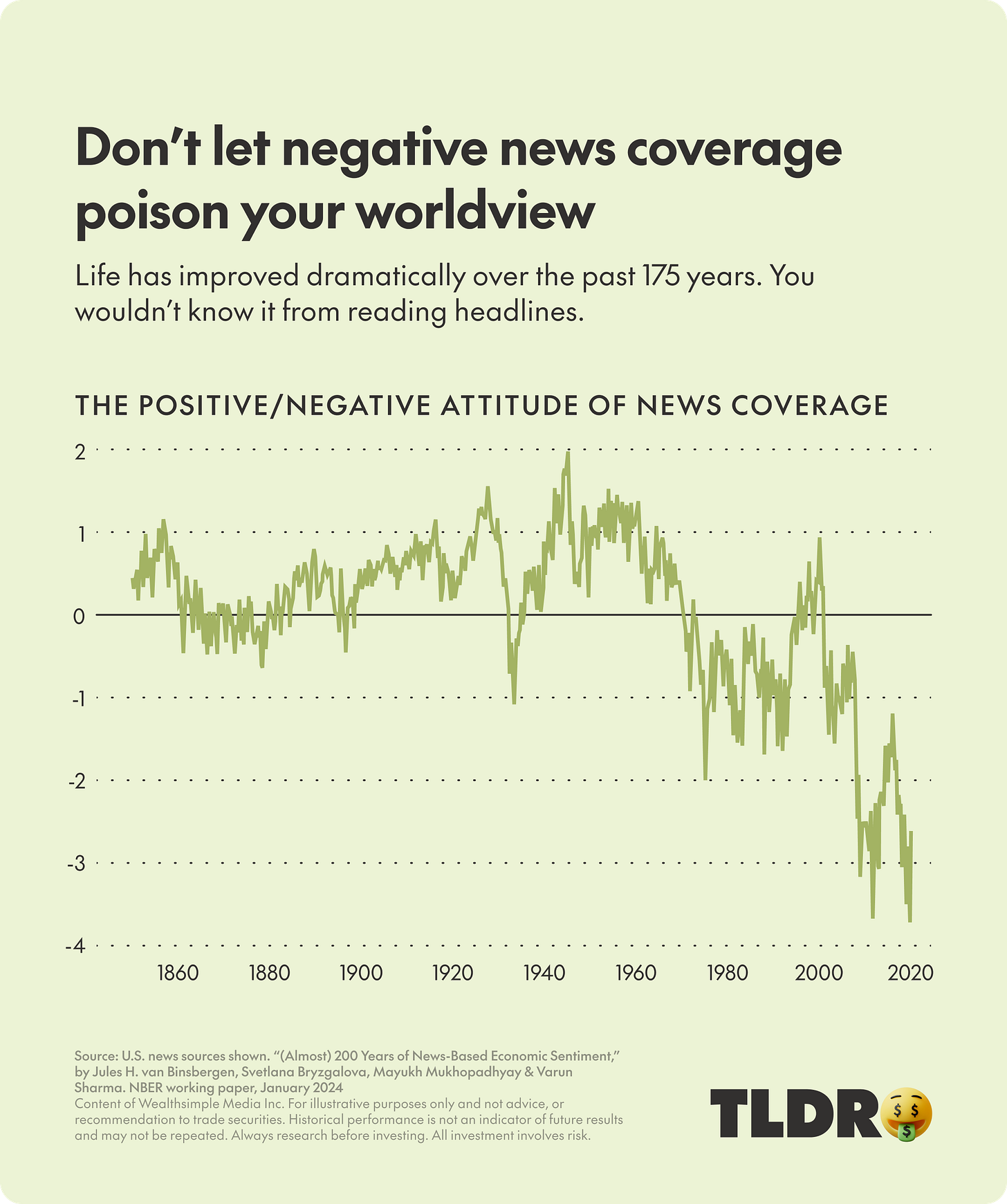
Media of the Week
Credit to the TLDR newsletter team at Wealthsimple for this. Media literacy has grown more important over the last 30 years, but it has not kept up pace with the breakdown of our information space that continues to be degraded with mis/disinformation and toxic, bad actors. Canada is not immune to this and it continues to get worse.




Thank you for a comprehensive article. With regard to digital sovereignty, I infer that ANY US software component into a Canadian sovereign cloud creates vulnerabilities. Are there many non-US software options? I’m not much of a computer nerd.