Weekly News Rewire - 17/01/26
Wiring you into the cyber news the week ending January 17
The Weekly New Rewire is a survey of cyber-related or adjacent news stories that I am following this week (or recently). A new research article that many of you are used to reading will be released next week, so stay tuned!
Please leave a comment if you think I missed anything.
Canadian News
RCAF wants more than 1,200 security personnel to protect F-35s, other planes
A significant reason for this is the digital infrastructure and data that the F-35 and other future air-based platforms require, which is a big reason why Secret Cloud is desperately needed and wanted to better manage and protect this data.
Hacks on, hacks off: How one coding dojo is preparing kids for the AI world
Canadian tech exits attract more American buyers than Canadian ones: Fasken report
The full Fasken’s Exit InSights report can be read here. For those working in the emerging technology and innovation space, this comes as no surprise, but this helps to quantify how much American buyers dominate this space and captures Canadian capital and intellectual property.
German submarine maker partners with AI firm Cohere in bid to build next Canadian fleet
Globe and Mail: “German submarine builder ThyssenKrupp Marine Systems is partnering with Canadian AI company Cohere to bring its technology aboard Canada’s next fleet of submarines, should TKMS win the multibillion-dollar contract.”
Cohere is the Canadian AI business that the Government of Canada loves because Cohere is very passionate about being Canadian and growing in Canada. Cohere’s tech is quite good from everything that I hear, I have no personal experience, so this is a good strategic move.
The Canadian Investment Regulatory Organization (CIRO) confirms that as a result of a sophisticated phishing attack, first disclosed in August 2025, approximately 750,000 Canadian investors have been impacted.
Canadian AI Data Centre Proposals: Enabling large-scale sovereign AI data centres
Innovation, Science and Economic Development Canada is inviting industry partners to submit proposals to help build large-scale AI data centres.
U.S. tech groups want to use USMCA to end the AI copyright fight
Telcos removing Huawei equipment left in the lurch after Trudeau kills cyber bill
Canadian telecom companies are removing Huawei equipment from networks following despite the prorogation of parliament that killed Bill C-26, which would have established a legal framework requiring equipment removal.
January 21 COVE Event: NATO and Canada | Accelerating Technology with Capabilities and Investment
Elon Musk’s X facing Canadian privacy probe over sexualized deepfake images
“Canada’s privacy watchdog is expanding its investigation into Elon Musk’s X Corporation in light of the company allowing its AI chatbot to generate sexualized images of women and children.”
Evan Solomon Wants Canada to Trust AI. Can We Trust Evan Solomon?
“The journalist-turned-minister says the tech will make us richer and regulation should be ‘light’”
CAF Cyber Forces have been active in the Philippines over the last few years. I have an article on the role of cyber in Canada’s Indo-Pacific strategy that’s been slowly in the works for a while now.
Have your business and logo featured in Canadian Cyber in Context with a sponsorship.
Canada Cyber Watch
While not all attacks are reported or receive media attention, any notable or open-source cyber attacks on Canadian organizations and any relevant cyber threat intelligence to Canada will be posted here. I only list Canadian Centre for Cyber Security’s (CCCS) alerts here and not all advisories, follow the full feed here.
ID Verification Service for TikTok, Uber, X Exposed Driver Licenses
An Instagram data breach reportedly exposed the personal info of 17.5 million users
NordVPN denies breach after alleged server leak surfaces on BreachForums
Russian APT28 Runs Credential-Stealing Campaign Targeting Energy and Policy Organizations
Flare uncovers phishing campaigns scamming Canadians with fake toll and parking violation texts
Alert - AL26-001 – Vulnerabilities affecting n8n – CVE-2026-21858, CVE-2026-21877 and CVE-2025-68613
LOTUSLITE Backdoor Targets U.S. Policy Entities Using Venezuela-Themed Spear Phishing
Chinese hackers targeting ‘high value’ North American critical infrastructure, Cisco says
Research and Op-Eds
Centre for International Governance Innovation:
Developing an Online Cybersecurity Literacy Awareness Module for Post-Secondary Students
What Canada’s AI Strategy gets wrong about sovereignty.
Op-ed by Joshua van Es that highlights that the government is repeating the mistakes I highlighted last year: sovereignty based on simply being in Canada is not enough to protect Canadian digital sovereignty.
Council of Canadian Innovators: Innovation as Power: The Choices That Will Define 2026
United States News
Chinese hackers targeted email systems of US congressional staff, people familiar say
The same thing happened to the House of Commons last year. I wouldn’t be surprised if it was part of the same campaign.
Lawmakers boost funding for NIST after proposed cuts
After the National Institute for Standards and Technology (NIST) originally faced a steep budget cut under Trump, House and Senate negotiators agreed to a $1.8 billion budget for NIST.
U.S. Weighs Expanding Private Companies’ Role in Cyberwarfare
Many of you may recall that I wrote about this back in October 2025. There have been indications that the US may be headed this way for the past year or two. There are strong arguments in favor and against the US authorizing private actors to conduct cyber operations against cyber threats, but in the end any favorable argument still requires oversight and a government which respects the rule of law to ensure that private actors are targeting actual threats and that their attacks do not disrupt other active operations. This is unlikely to occur with the current US government.
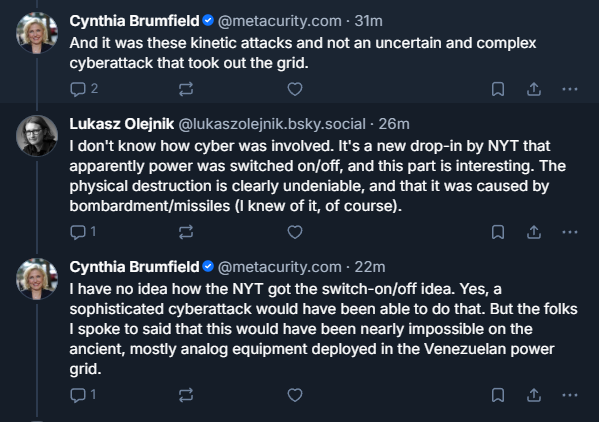
Cyberattack in Venezuela Demonstrated Precision of U.S. Capabilities
Last week I had stated that a lot of the chatter on cyber operations used for effects may have been overblown, but additional reporting continues to hint that the US used cyber operations to turn off and on Venezuela’s power despite the physical damage to the infrastructure. Despite this, a lot of this remains speculative and most experts are not talking about the use of cyber operations to take out the power because that is the least likely use of cyber operations in such an operation.
It is important to note that a lot of news agencies are running with this because of Trump’s comment that ““It was dark, the lights of Caracas were largely turned off due to a certain expertise that we have….” In the best of circumstances Trump is an unreliable narrator, in the worst of circumstances he’s a pathological liar, so we must take everything said by him with the world’s largest grain of salt.
In a highly risky military special operations like the one to kidnap Maduro, it is not uncommon to layer effects simultaneously, which the article alludes to having occurred and increases the likelihood of success. As a result, it is very much possible that the US used a cyber operation to target Venezuela’s in addition to physically damaging infrastructure. In the end, this remains speculative and no one is arguing that this cyber couldn’t be used this way, but Venezuela’s old, analog power grid and the evidence of physical damage suggests that it was not cyber or cyber operations were only used in part. Instead, what is more likely the case is cyber operations used for intelligence and taking out air defence as suggested in the New York Times article.
Personal Details of Thousands of Border Patrol and ICE Goons Allegedly Leaked in Huge Data Breach
Sensitive details of around 4,500 ICE and Border Patrol employees have allegedly been released by a whistleblower the murder of Renee Nicole Good. The website has been targeted with rolling DDoS attacks in an effort to take the website offline.
The Federal Trade Commission finalized an order with General Motors and OnStar settling allegations that they collected, used, and sold consumers’ precise geolocation data and driving behavior data from millions of vehicles without adequately notifying consumers and obtaining their affirmative consent.
GDIT tapped to deliver zero-trust security solution at nearly 200 Air Force bases
General Dynamics Information Technology will upgrade the networks at 187 Air Force bases with a zero trust-based capability, the company announced Wednesday.
International News
Infamous BreachForums forum breached, spilling data on 325K users
BreachForums was one of the most well known criminal hacking forums on the Internet and was one of the largest marketplaces for stolen data, hacking tools, and other illicit criminal services. The leaker of this data is allegedly a mentor of many of the individuals involved in these activities, but decided to turn on them once they “[turned] against the French Nationa and targeted France and French nationals.
Denmark blames Russia for cyberattacks on water utility that left houses without water
Russian cyber attack caused physical damage to water infrastructure in Denmark: “The water company said the attack caused pipes to burst, leaving homes temporarily without water.”
Massive cyberattack on Polish power system in December failed, minister says
Poland's power system faced its largest cyberattack in years in the last week of December that also followed a different pattern, the country's energy minister said on Tuesday.
Belgian hospitals AZ Monica hit by cyber attack
The two Belgian branches of AZ (General Hospital) Monica in Deurne and Antwerp were hit by a cyberattack on Tuesday, January 13th. All servers were shut down, forcing the cancellation of the surgery and outpatient clinic schedules. It is not yet clear who is behind the attack and what demands the cybercriminals are making. (Translated by Google)
QR codes a powerful new phishing weapon in hands of Pyongyang cyberspies
Keeping Syria connected during war
A Syrian Telecom engineer's account told his story during the war; what was behind internet shutdowns? And what happened during students’ exams?
Hacker Claims To Sell 8 Million Records Worth of Armenia’s Government Mailing Data
Dutch man sentenced for infecting port with malware
A Dutch man was sentenced to seven years in prison for paying an Antwerp port working to connect a USB drive to a port network, which was used to import over 200 kilos of drugs into the Netherlands.
“Nissan has 5 days before we leak their data,” attackers threaten
Jaguar Land Rover reports fiscal Q3 sales slump following cyberattack
Perhaps one of the most clear-cut cases of how a major cybersecurity incident can lead to a business disaster. Cybersecurity is often one of the first times to lose funding when times get tough, but it’s what’s needed more than ever when times are tough.
Suspected ransomware attack threatens one of South Korea’s largest companies
Ukraine pins AI-powered LameHug malware attacks on defense sector to Russian-backed APT28 group
China Bans Cybersecurity Products From Top US, Israeli Firms
AI and RAM Costs: Long story short: AI is making all technology more expensive because DRAM (computer memory) is in short supply.
Q&A
Every week, I will answer any questions that I receive through the Weekly News Rewire Slido here. Slido allows readers to anonymously submit questions and vote on those they would like answered.